Instagram Security Incident: Password Reset Emails, Data Exposure, and What It Means for Cyber Risk
Over the weekend, you might’ve been one of the unlucky few (millions of) Instagram users who received a password reset email. Now, if you’re anything like us, that probably set alarm bells ringing - your social media accounts being breached is the 2026 version of a diary being read.
Naturally, as more and more people got the email, and then security company Malwarebytes posted on Bluesky, claiming hackers had “stole the sensitive information of 17.5 million Instagram accounts, including usernames, physical addresses, phone numbers, email addresses, and more”, and that it was now up for sale on the dark web, concern started to snowball.
To some people, a social media breach may not seem like a big deal. It’s only Instagram, for example, right? Only, it IS a big deal, and it can cause real-world damage now, too. You only have to look at Sunday night, when Manchester United captain Bruno Fernandes’ social media account was hacked and offensive slurs, as well as criticism of the club’s ownership, were posted, prompting the club to issue a statement.
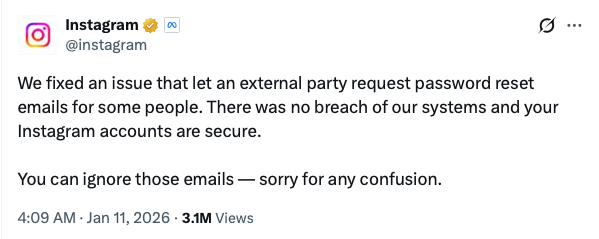
With questions being raised about user data exposure and account security, Meta moved quickly to state that Instagram’s internal systems were not breached and that the incident stemmed from an issue that allowed external parties to trigger password reset emails, which has since been resolved.
However, independent reporting indicates that account metadata, including usernames, email addresses and phone numbers, may have been exposed through other means and linked to the surge in reset activity. And, if so, that could (and should) be ringing warning bells in your head.
What Happened
Over the weekend of the 10th-11th January 2026, users across multiple regions reported password reset emails they had not requested. The emails originated from Instagram’s legitimate domain, which increased concern that accounts were being actively targeted rather than spammed.
While Meta denies a platform breach, the presence of circulating user data highlights how exposed identifiers can be leveraged to abuse account recovery workflows on a large scale.
What We Know So Far
• Users received legitimate Instagram password reset emails they did not request
• Meta has stated there was no breach of Instagram’s internal systems
• Reports suggest account metadata may be circulating externally
• Abuse of account recovery workflows appears to be involved
What Remains Unclear
• The original source of the exposed account data
• Whether the data was scraped, leaked, or aggregated from multiple sources
• How widely the dataset is being actively exploited
Why This Matters
Account recovery is a high-value attack surface: Password reset mechanisms are designed for convenience and automation. When attackers gain access to large volumes of contact data, these workflows can be abused without compromising core authentication systems.
Metadata exposure enables secondary attacks: Email addresses and phone numbers are often sufficient to support phishing, SIM-swap attempts, credential stuffing, and social engineering. Even without passwords, the operational risk is significant.
Legitimate alerts can still be weaponised: When real system emails are triggered at scale, users struggle to distinguish between genuine security events and malicious activity. This increases confusion and slows response.
What Organisations Should Do
• Review account recovery and password reset logic for abuse patterns
• Rate-limit and monitor automated reset requests
• Treat exposed user metadata as actionable risk, not low-impact leakage
• Strengthen user guidance around verifying security communications
• Encourage app-based multi-factor authentication by default
What Users Should Do
• Do not engage with password reset emails you did not request
• Enable app-based multi-factor authentication
• Change passwords reused across services
• Monitor accounts for unusual activity
Why This Matters Beyond Social Media
Incidents like this are often dismissed because they involve consumer platforms, or get put down to ‘just being Instagram’.
That’s a mistake.
Those same recovery workflows, metadata exposure risks, and automation logic exist in enterprise SaaS platforms, identity providers, and customer portals. So if attackers can trigger recovery actions or correlate exposed identifiers at scale, the impact on business systems can - and will - be far more severe. Especially in future attempts.
The Bigger Picture
Over the past year, several high-profile incidents have demonstrated that attackers are increasingly targeting identity workflows rather than perimeter defences. Abuse of legitimate workflows, such as password resets, support tickets, MFA fatigue, and recovery APIs, is attractive because it sits at the intersection of automation and trust - and, perhaps crucially, does so without a single firewall being crossed.
From our work with organisations managing identity and access at scale, incidents like this are rarely isolated. They expose assumptions about recovery processes, monitoring coverage, and the speed at which an intrusion is detected. So, as systems become increasingly interconnected, weaknesses in identity and recovery logic can rapidly spread across services and users.
For organisations, resilience now includes securing recovery paths, metadata handling, and user trust, not just core infrastructure.
We’ll be keeping an eye out for any increased attack attempts following this.